The number of ransomware attack attempts targeting Microsoft customers globally increased dramatically last year, according to Microsoft’s Digital Defense Report released on October 15. However, advances in automatic attack stopping technology have resulted in fewer attacks reaching the encryption stage. .
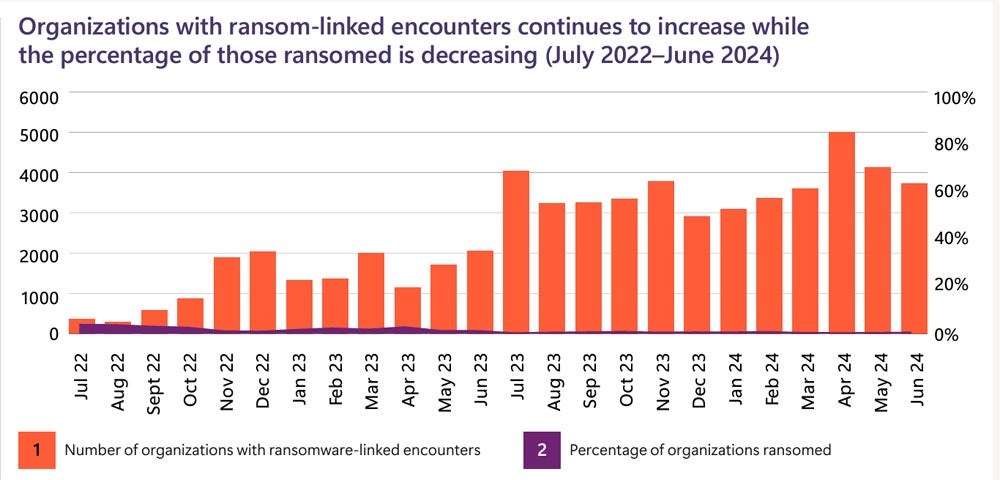
Microsoft reports that 600 million cybercrime and nation-state attacks occur every day. Ransomware attempts increased 2.75x, while the success rate of attacks involving data encryption and ransom demands decreased 3x.
Important types of attacks include deepfakes and e-commerce theft.
“We track more than 1,500 unique threat groups, including more than 600 nation-state threat actor groups, 300 cybercrime groups, 200 influence operations groups, and hundreds of others,” Microsoft said. The top five ransomware families (Akira, Lockbit, Play, Blackcat, and Basta) accounted for 51% of documented attacks.
According to the report, attackers most often exploit social engineering, identity compromise, and vulnerabilities in public applications or unpatched operating systems. Once inside, they often install remote monitoring tools or tamper with security products. Specifically, 70% of successful attacks involved remote encryption and 92% targeted unmanaged devices.
Other main types of attacks include:
- Infrastructure attacks.
- Cyber-based financial fraud.
- It’s an attack on the e-commerce space, where credit card transactions don’t require the card to be physically present.
- personification.
- Deepfake.
- Account takeover.
- Identity and social engineering attacks – most (99%) were password theft attacks.
- SIM swap.
- Help desk social engineering where attackers impersonate customers to reset passwords or connect new devices.
- Credential phishing, especially through the Phishing-as-a-Service project. These are often triggered by HTML or PDF attachments containing malicious URLs.
- A DDoS attack that caused a worldwide outage earlier this year.
Antivirus tampering was a major player in previous years as well. In 2024, more than 176,000 incidents detected by Microsoft Defender XDR involved tampering with security settings.
Note: Ransomware attackers can target backup data to force payment.
Financially motivated actors at the state level share tactics.
Both financially motivated threat actors and nation-state actors are increasingly using the same information thieves and command-and-control frameworks, Microsoft said. Interestingly, financially motivated attackers have launched cloud identity compromise attacks, a tactic previously associated with nation-state attackers.
“This year, the lines between state-sponsored malicious activity and cybercrime activity have blurred, with nation-state threat actors increasingly using criminal tools and tactics, and even criminals themselves, to pursue their own interests,” the report said. It was revealed.
Microsoft tracks major threat actor groups in Russia, China, Iran, and North Korea. These countries may leverage financial threat actors for their own benefit or turn a blind eye to their activities within their borders.
The ransomware issue highlights the link between nation-state activity and financially motivated cybercrime, according to Tom Burt, Microsoft’s vice president of customer security and trust. This problem is further exacerbated by countries exploiting these operations for profit or failing to take action against cybercrime within their borders.
Expert Evan Dornbush, a former NSA cybersecurity expert, offers his perspective on the matter.
“This report highlights one trend that currently receives little attention but is likely to define the future of cyber: how much money criminals can make,” he said in an email to TechRepublic. “According to a Microsoft report, the government sector only accounts for 12% of attackers’ target set. “The majority of victims are in the private sector,” he said.
The top areas attacked by nation-state threat actors this year are:
- that.
- education .
- government.
- Think tanks and NGOs.
- transit.
Both attackers and defenders use generative AI.
Generative AI poses new questions. Microsoft recommends limiting generative AI’s access to sensitive data and applying data governance policies to its use of that data. This report outlines the significant impact AI will have on cybersecurity.
- Both attackers and defenders are increasingly using AI tools.
- State actors can use AI to create deceptive audio and video.
- AI spear phishing, resume scams, and deepfakes are now commonplace.
- Existing methods of limiting foreign influence activities may no longer work.
- AI policies and principles can mitigate some of the risks associated with using AI tools.
- Although many governments agree on the need for security as a critical element of AI development, each government pursues security differently.
“The volume of attacks must be reduced through effective deterrence, and industry must do more to deny the efforts of attackers through better cybersecurity, but this must be done in parallel with government action to impose consequences that further deter attacks,” Burt said. .” he said. “The Most Harmful Cyber Attacks”
How Organizations Can Prevent Common Cyber Attacks
The Microsoft report includes steps organizations can take to prevent specific types of attacks. TechRepublic has compiled some actionable insights that apply across the board.
- Block attacks at the technology layer. That means implementing policies like multi-factor authentication and attack surface reduction.
- Likewise, use the “Basic Security” setting, which sets multi-factor authentication to required.
- Use strong password protection.
- Test pre-configured security settings, such as security defaults or managed conditional access policies, in report-only mode to understand their potential impact before going live.
- Classify and label sensitive data and put in place DLP, data lifecycle, and conditional access policies for high-risk data and high-risk users.
Microsoft implemented its Secure Future Initiative this year following the July 2023 breach of Microsoft government email accounts in China.
