The 2024 vacation season showed a complicated and evolving threat to DDOS (DDOS) attacks. This year’s trend included advanced tactics such as selections between the increase in DDOS-For HIRE operating, the large DDOS botnet council by the script children, the political motivated attack campaign, and the threats of different developments of the CDN (Content Delivery Network) protection. .
The 2024 vacation season showed a complicated and evolving threat to DDOS (DDOS) attacks. This year’s trend included advanced tactics such as selections between the increase in DDOS-For HIRE operating, the large DDOS botnet council by the script children, the political motivated attack campaign, and the threats of different developments of the CDN (Content Delivery Network) protection. .
Azure’s 2024 vacation season attack environment
During the holiday season, we mentioned the change of last year’s attack pattern and emphasized how malicious actors continue to improve tactics to bypass DDOS protection.
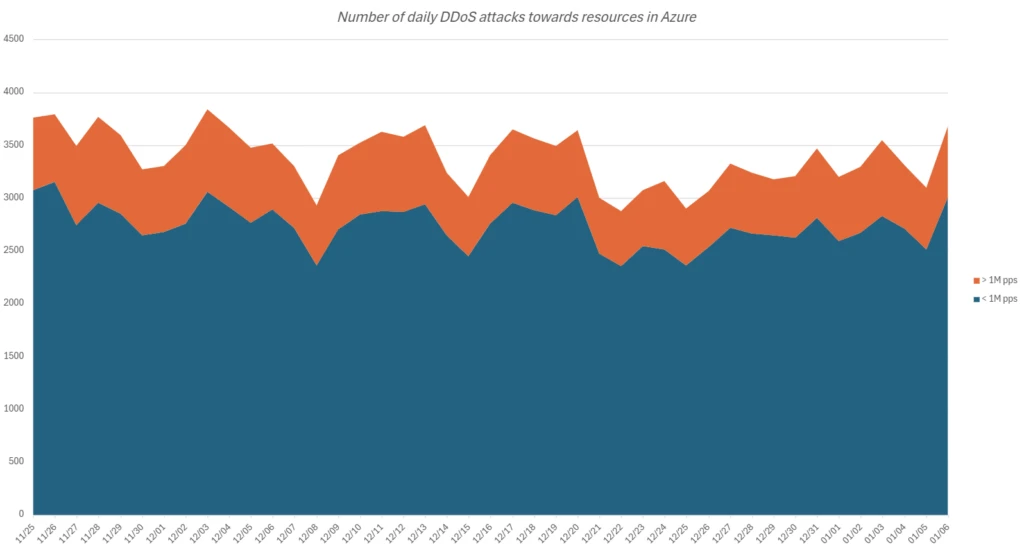
Daily attack volume
Azure’s security infrastructure alleviates up to 3,800 attacks every day. Large attacks of more than one million packets (PPS) per second construct about 20%of them, similar to last year’s analysis. A volume attack that exceeds 10m PPS is only 0.2%of all attacks, reflecting the goal of minimizing the attacker’s resources and avoiding detection.
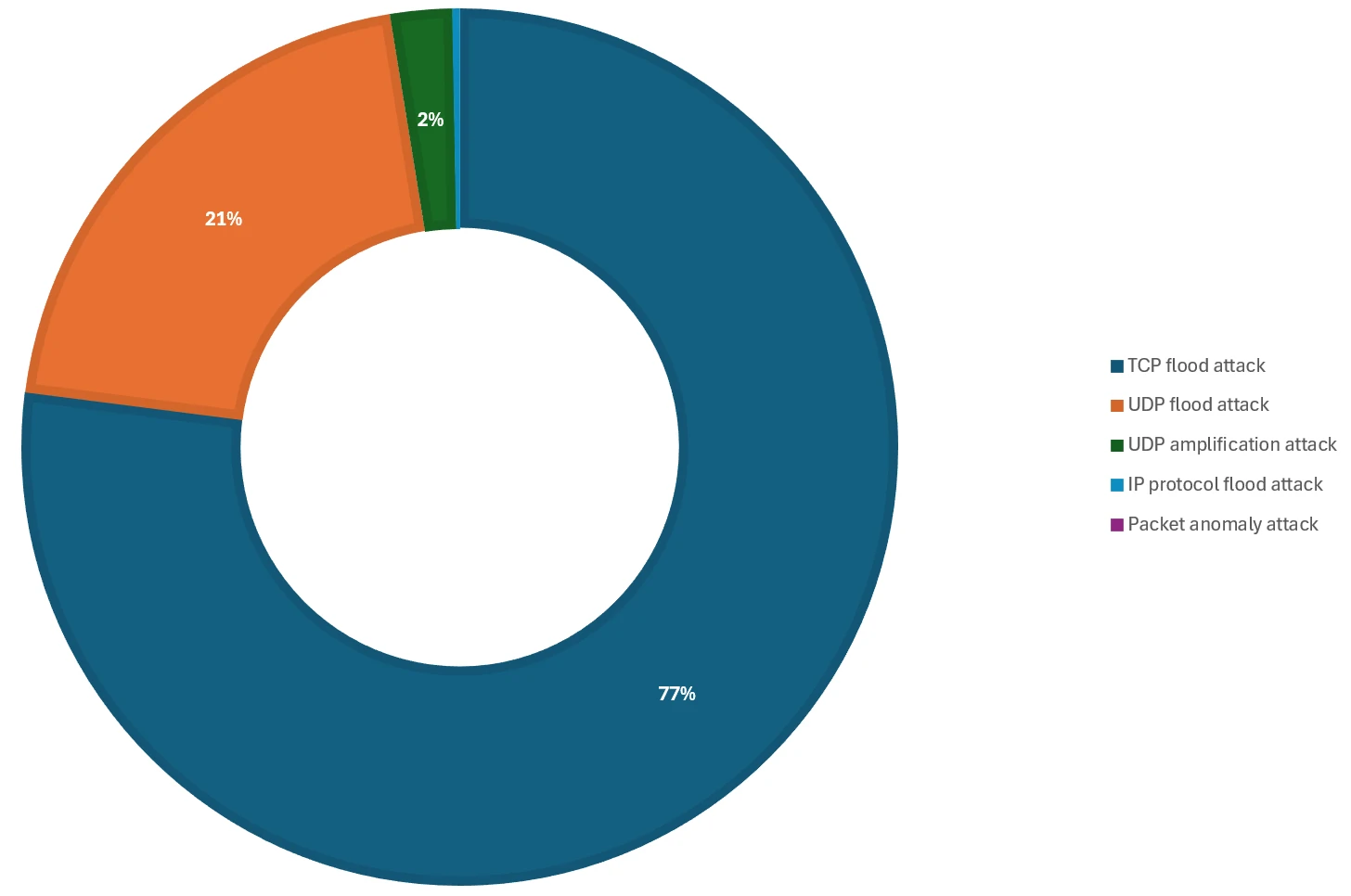
Attack protocol
In the 2024 vacation season, the TCP -based attack (transmission control protocol) was mainly used, accounting for 77%of the attacks for various web applications and resources. This is in contrast to last year, when UDP -based attacks (user data gram protocols) accounted for almost 80%of attacks on games and other resources. This year’s major TCP attack vectors were TCP SYN (Synchronize) and ACK floods.
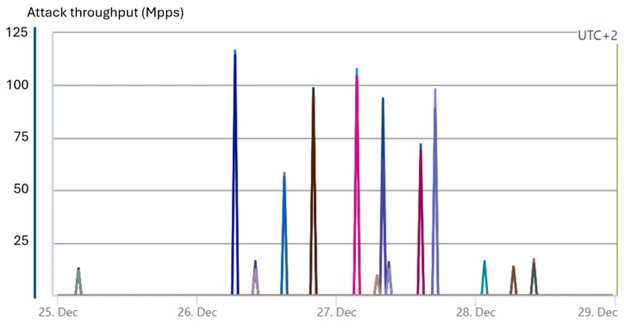
Azure blocks a large Typhone attack
A tremendous attack on game resources has reached 125 million pp from several waves. The signature with Typhon Botnet has been completely relaxed by Azure’s defense.
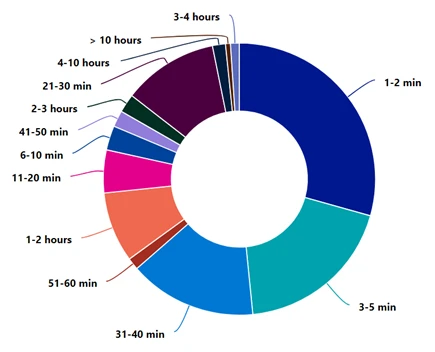
Attack duration
This time we have witnessed the same tactics as we are trying to bypass our DDoS easing strategy by starting a burst or short -term attack. 49%of all attacks lasted for up to 5 minutes and 83%of attacks lasted less than 40 minutes. It is insight to understand that we need to start effective easing as soon as we can relax the DDOS relief measures we implemented to protect the application.
Political motivation and DDOS-HIRE SURGE
This vacation season, Azure’s attack trend reflects global patterns. Political motivation attacks led by designated scientific tensions persist. DDoS threats still remain a big concern as new actors are confused using available tools.
Often, the injury of the DDOS-For Hire service, called stress and boots, has gained great popularity among attackers. This platform, which can be easily accessible in the Cyber Crime Forum, can democratize the ability to start a strong DDOS attack and achieve less sophisticated criminals at a minimum cost. In recent years, all the availability and use of these services have increased. During the holiday season, the International Law Executive Agency performed operations such as operating poweroffs in December, arresting three individuals and closed 27 domains related to the DDOS-For Hire platform. Despite these efforts, the DDOS stress system continues to thrive to provide a variety of attack methods and power and maintain the prevalence.
Preparation in 2025
The 2024 vacation season emphasized the continuous threat of DDOS attacks. Organizations need to improve cyber security strategies to cope with this evolving threat in the new year. In 2025, it is important to be bound to strengthen defense and new tactics. Azure’s elasticity to high -end DDOS threats emphasizes the importance of strong security measures to protect digital assets and ensure business continuity.
Identify the exposure point
Find exactly what applications are exposed to the public Internet. Evaluating the potential risks and vulnerabilities of these applications is important for understanding the most vulnerable location for attack.
Normal work recognition
Be familiar with the normal behavior of the application. Azure provides monitoring services and best practices to gain insight into the health of the application and effectively diagnose the problem.
Attack Scenario Simulation
Running a regular attack simulation is an effective way to test the response of a service for potential DDOS attacks. Check that the service or application continues to work as expected during the test and there is no confusion about the user experience. In terms of technology and process perspective, identify gaps and integrate DDOS response strategies.
Strong protection guarantee
Because there is a high risk of DDOS attack, you need to have DDOS protection services such as Azure DDOS protection. This service always provides the entire visibility of DDOS attacks using traffic monitoring, automatic attack alleviation, adaptive real -time tuning and real -time remote measurement, monitoring and warning.
Class security implementation
For comprehensive protection, place a multi -layer defense by placing Azure DDOS Protection with Azure Web Application Firewall (WAF). The Azure DDOS Protection secures a network layer (Layer 3 and 4), and Azure WAF protects the application layer (layer 7). This combination ensures protection of various types of DDOS attacks.
Warning composition
Azure DDOS protection can identify and alleviate attacks without user intervention. A warning about the activity relief can tell you about the state of the protected public IP resources.
Establish a response plan
Set a DDOS response team with a clearly defined role and responsibility. The team should be good at identifying, relaxing and monitoring attacks as well as adjustment with internal stakeholders and customers. Use the simulation test to identify the difference in response strategies so that the team can prepare for various attack scenarios.
We are looking for expert support
If an attack occurs, it is important to reach a technical expert. Azure DDOS Protection customers can access the DDOS Rapid Response (DRR) team for attack and post -support. After attacking, keep monitoring resources and perform fragrance analysis. Apply learning to improve DDOS response strategy to ensure better preparation for future events.
Behavior
In the 2024 vacation season, the DDOS-For Hire operation, large-scale botnets and political motivated campaigns increased significantly, emphasizing the evolving threat of DDOS attacks. This threat emphasizes the need for strong DDOS protection and DDOS response plan. Azure supports the organization to be ahead of this threat. Customers must distribute Azure DDOS protection with Azure Web Application Firewall (WAF) to enable multilayer protection. Customers also need to make remote measurement and warning functions effectively monitoring and responding to activity alleviation.
